UAC Bypass in System Reset Binary via DLL Hijacking
To continue our journey in the realm of bypassing UAC (see previous work here), we’ve decided to investigate Windows Server 2019. Please note this blog post is not a UAC primer but if you need to learn more about the subject, we think Wikipedia is a good place to start. The following is the process used to find a new UAC bypass in systemreset.exe binary using DLL Hijacking method. The technique was tested on Windows Server 2019 Version 1809 (OS Build 17763.404) and its still valid as of this writing.
Examining the manifest file shows the binary “autoElevate” property is set to true:
So we set Procmon64.exe with the following self-explanatory filters:
We then let it run while executing systemreset.exe and quickly notice the binary is trying to load FVEAPI.dll from a user-controlled folder in high-integrity context due to the PATH variable:
We built a relatively simple DLL that would spawn calc.exe when PoppingCalc() function gets invoked using DllMain and then use rundll32.exe to test it:
Now executing the problematic binary with the newly created DLL in place shows the following error message:
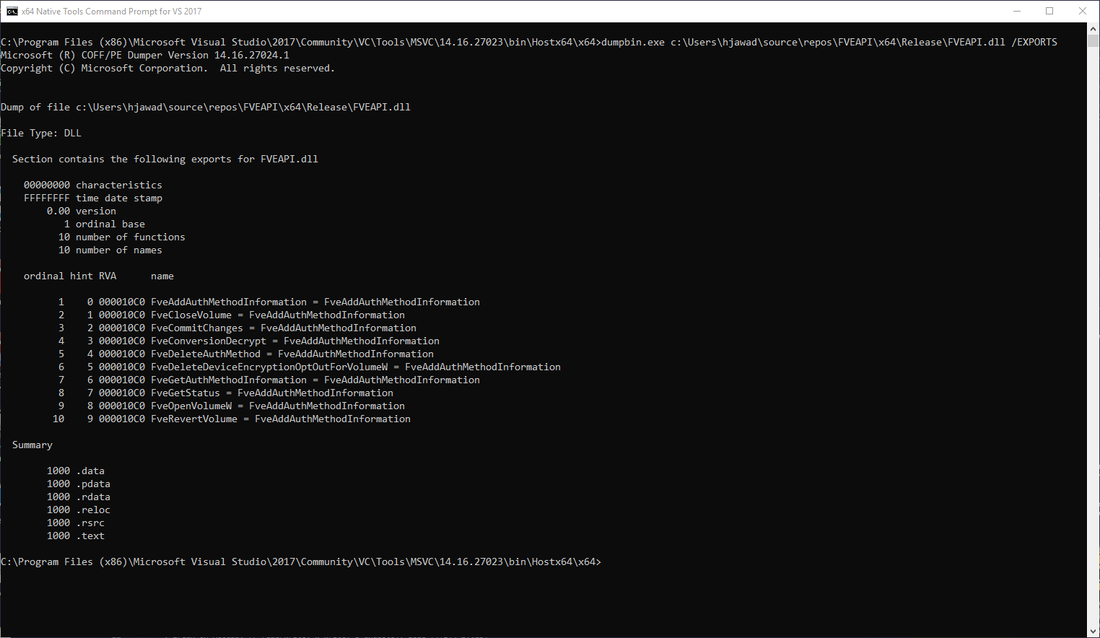
As the error message suggests, ResetEngine.dll failed to locate FveGetStatus() function in FVEAPI.dll, using this information we identify the list of exported functions required by ResetEngine.dll via the import table:
We update FVEAPI.dll with the missing exported functions and then confirm functionality via dumpbin.exe. The full proof-of-concept code can be found here.
Here is the demo:
We did report this to MSRC and received the following response:
This particular technique can be remediated by setting the UAC level to “Always Notify” or taking away local administrative rights. We hope you’ve learned something from this blog post and feel free to reach out at labs@activecyber.us if you have any questions.
Disclosure Timeline
03-28-19: Report sent to MSRC
03-28-19: MSRC acknowledged report and case manager was assigned
04-01-19: MSRC responded stating they do not service UAC bypasses and consider the matter resolved
04-10-19: Blog post released