|
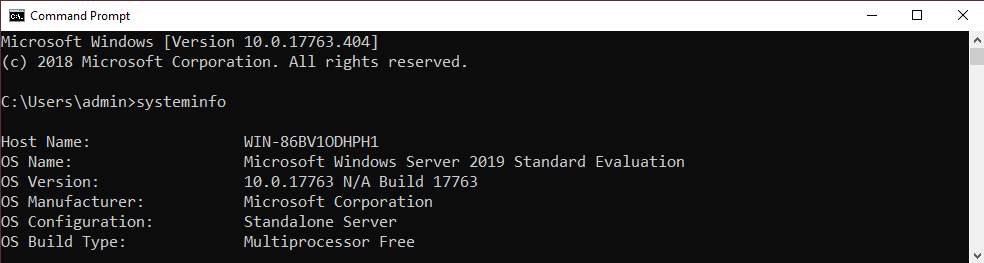
To continue our journey in the realm of bypassing UAC (see previous work here), we’ve decided to investigate Windows Server 2019. Please note this blog post is not a UAC primer but if you need to learn more about the subject, we think Wikipedia is a good place to start. The following is the process used to find a new UAC bypass in systemreset.exe binary using DLL Hijacking method. The technique was tested on Windows Server 2019 Version 1809 (OS Build 17763.404) and its still valid as of this writing.
0 Comments
|
Archives
June 2024
ACTIVELabs was created in 2018 to hunt and research undiscovered vulnerabilities, report them to vendors via responsible disclosure programs, publish advisories, develop and validate new patches, and to share this information for the advancement of the cybersecurity community. ACTIVELabs was established with the mission of securing our ever-growing client base, partnerships, and the technology community as a whole.
We are actively providing the community with verified findings and research that leads to the creation of new Common Vulnerabilities and Exposures (CVEs) and updates to the National Vulnerability Database (NVD). For a full listing of all of our Advisories, visit our GitHub page here. |
|
©2022 ACTIVECYBER, LLC | All rights reserved | Privacy Policy
|

 RSS Feed
RSS Feed

